
Cybercrime is up – more than 600% since March 2020.
As the pandemic reshaped the workforce and the workspace, cybercrime evolved apace leaving companies around the globe facing a rising tide of new threats increasing both in number and sophistication. Combined with an IT labor shortage of nearly half a million jobs, the challenge of doing more with less in-house talent has never been greater.
Meeting this challenge head-on requires more than just doubling down on beating cybercriminals at their own game – it’s going to mean breaking the rules altogether and putting security professionals on offense on their own terms. With an industry-first Attack Tracing and Intercept (ATI) approach, Spyderbat delivers just what security operations teams need to turn the dynamic around.
Getting the Full Picture with Spyderbat
“Nobody wants more alerts” is how premiere security analyst Richard Stiennon characterizes the current trend of security industry burnout. But for more than two decades, network security platforms have had little else to offer increasingly beleaguered IT teams besides repackaged intrusion detection systems (IDSs) that leave them playing an endless game of alert-based Whac-A-Mole.

Spyderbat’s approach pulls the plug on this game entirely by giving security teams a comprehensive, real-time vantage point on attacks as they occur and not behind the industry-average 280-day intrusion lifecycle. Traditional security platforms begin recording information only after a potential threat has been detected. They can only react after an attack has already begun. But why settle for a single, incomplete frame when you can capture the whole story live?
Spyderbat doesn’t sit idly by waiting for attacks to arrive. Instead, Spyderbat maintains an exhaustive record of the totality of system calls establishing a universal trace on which security teams can see meaningful, causal connections between events that would otherwise be lost in the logs.
Benefits of Using Spyderbat
Spyderbat equips security teams with a force multiplier providing three decisive advantages over traditional, reactive security solutions.
1. Forget the Chase and Skip to the Capture with Universal Tracing
With intrusion dwell times now measured in months across the industry, log-based security controls demand that every analyst be like Sherlock Holmes reconstructing complex event narratives with just a few meager clues.
While tedious detective work makes great fiction, out in the real world, we’d rather skip to the end – intruders identified and shut down at the point of entry. With Spyderbat, you can spoil the plot every time.
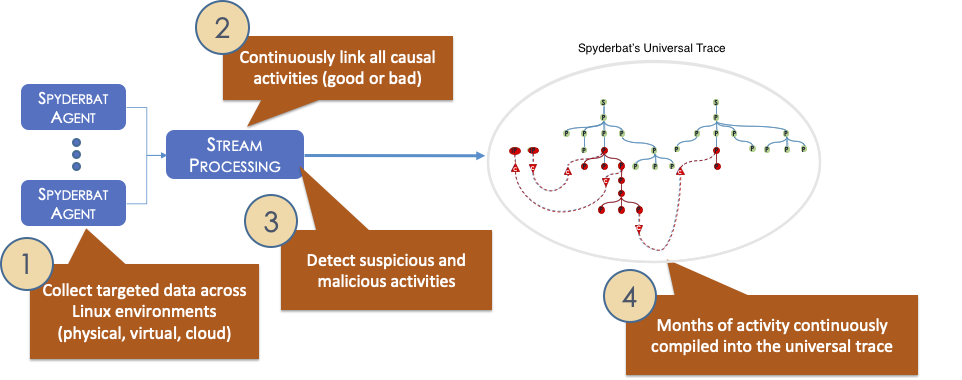
Universal tracing eliminates the burden of manual inference that stymies security workflows. When you have a living record of all system calls, you can immediately see the whole narrative of a security intrusion that may span multiple systems, user sessions, and even months.
2. Crush Dwell Times
As counterintuitive it seems, the chief culprit in extended dwell times is most often an excess of data rather than a lack of it. False positives currently account for more than half of the alerts that security teams need to triage.
Viewed from the overhead perspective of Spyderbat’s universal trace, false positives exhibit no causal connections. They tell no story and can be swiftly and confidently dismissed, decimating dwell times for credible threats.
3. Empower the Human Analyst Behind the Software
With an IT labor drought on the security landscape for the foreseeable future, companies can’t afford to hire their way out of new security challenges. Those who will thrive rather than just survive won’t task their teams with trying to beat a rigged game of detection and response.
They’ll rig the game themselves.

Spyderbat capitalizes on the talents of the human users. Human users are able to cut through the white noise of false positives and interminable logs.
Intruders will come to play hide-and-seek only to find that they can no longer hide.
Start Attack Tracing with Spyderbat for Free
See for yourself how Spyderbat can put your security teams back in the driver’s seat.
Get a free trial of the Community Edition.
Write a comment