By scanning network or log data for exploit strings, your security controls will generate a high number of false positives (attempted attacks that do not succeed). Attackers are already throwing exploit strings against the wall to see what sticks. Most will fail. It is useless, if not impossible, to investigate each use of the exploit to see if it is successful. Some security controls will attempt to correlate exploit indicators with successful behaviors, but correlation is not causation. This approach still generates false positives because secondary behaviors exhibited by the application become erroneously connected with a previous exploit indicator (which we already established are voluminous).
Detect only successful log4j attacks
Spyderbat differs from other solutions by generating a complete web of causal activity.
To understand causal activity, consider the following sequence of events:
- systemd launches sshd.
- sshd receives an incoming network connection.
- sshd launches a bash shell due to receiving the network connection.
- The command ‘id’ is executed in the bash shell.
In this example, the ‘id’ command is causally connected to the network connection; it would not have happened without that network connection.
Every system interaction is caused by something; Spyderbat captures these interactions and their causal relationships into a living graph as they occur. Here is an example of the above sequence of activities.

Spyderbat’s Causal Tree captures an accurate and complete sequence of causally-related activity. Each line represent
- An S-node represents a system. A Causal Tree may cross multiple systems.
- A P-node represents a process.
- A C-node represents a network connection.
The grey badges capture the effective user. We see the effective user changed to ‘douglas’ after the network connection was received by the sshd process.
What we know about the log4j exploit
In case you’ve been hiding under a rock for the last week, CVE-2021-44228 is a vulnerability in the Java Naming and Directory Interface (JNDI) in the widely used log4j library that enables remote command execution (RCE). When exploited, the attacker invokes an outbound communication using the Lightweight Directory Access Protocol (LDAP) or JAVA Remote Method Invocation (RMI) to retrieve and execute a malicious JAVA class from a machine controlled by the attacker. After a successful log4j exploit attempt, there will be an LDAP or RMI outbound request followed by a secondary outbound network connection (with optional DNS requests). Spyderbat avoids generating false positives by recognizing the causal relationship of the outbound connections with a common parent java thread.
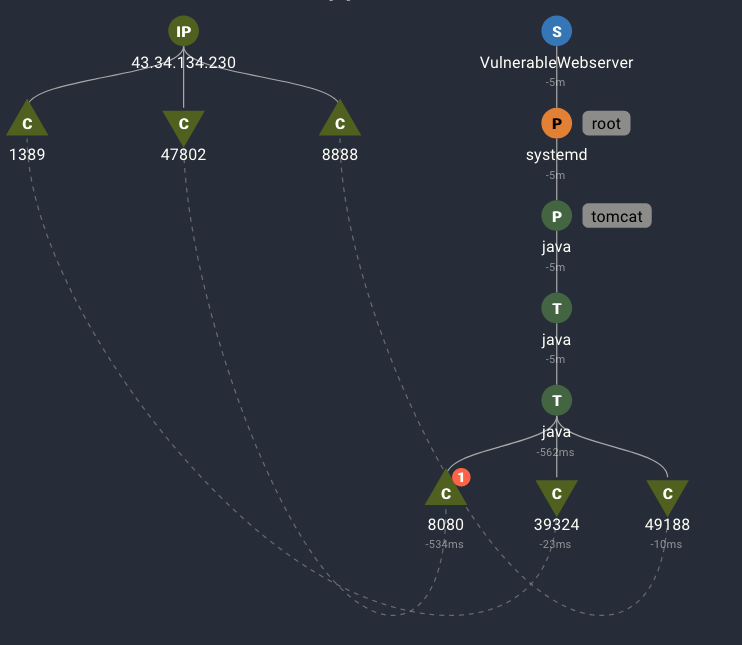
In the above image, we see Spyderbat capturing an inbound request received by a JAVA thread (a ‘T’ node in the graph) on port 8080, which generates two outbound connections on port 1389 and port 8888. While there may be many other inbound and outbound network connections occurring at the same time, Spyderbat’s understanding of causal connections recognizes their distinct relationship. This results in three advantages:
- Spyderbat’s analytic is not prone to false positives since it will not be triggered by unrelated network connections occurring within the same time period. A
- Spyderbat user is presented with a focused view of the causal activity captured by Spyderbat, removing noise from the many other extraneous activities occurring at the time.
- Any subsequent causal activity is tracked and captured by Spyderbat, removing uncertainty and the time required to fully investigate the attacker’s full impact.
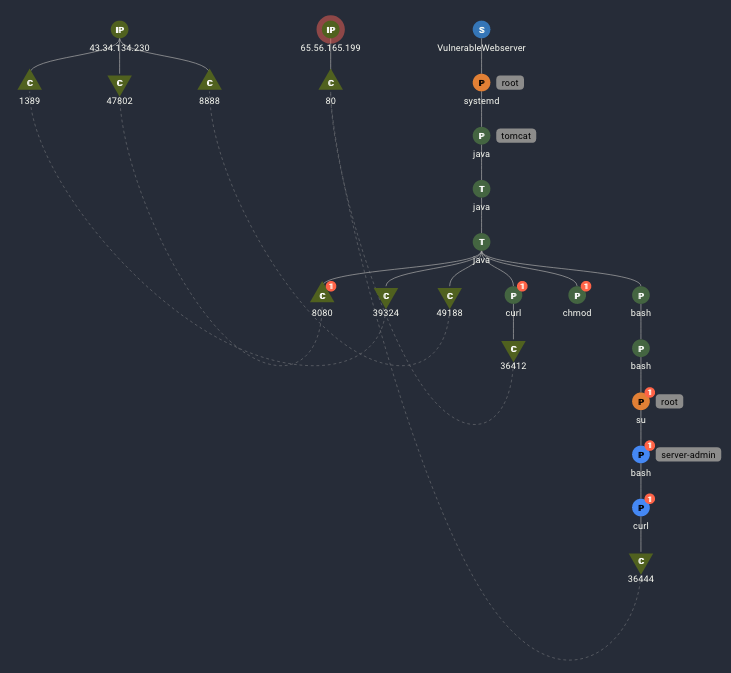
For example, the image below shows the initial successful log4j exploit, followed by subsequent activity including downloading and executing additional code and escalating privileges.
How to set up Spyderbat to detect successful log4j exploits
To find evidence of the behavior exhibited by a successful exploit attempt, after logging into Spyderbat click on ‘Search’ and type into the query string:
schema:"model_connection" AND direction:outbound AND proc_name:java AND NOT "127.0.0.1" AND NOT "::1"
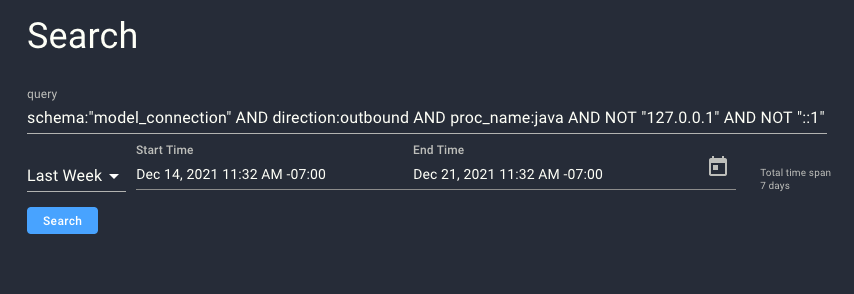
Click ‘Search’.
If the search result is “No Records Found” – that’s a good thing! It means Spyderbat did not find any evidence of a successful exploit attempt.
Click ‘Save as Dashboard Card’.
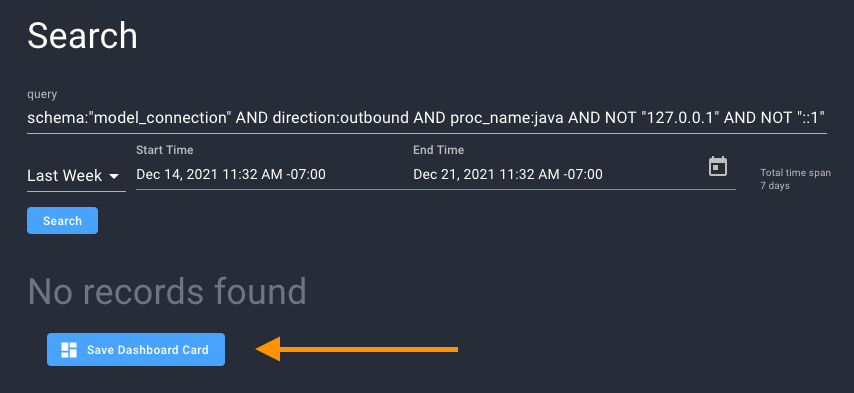
Change the name to a friendlier title. Leave the Dashboard Card Type as “Process”.
To set up a notification to be alerted or take action when any evidence is discovered, refer to https://www.spyderbat.com/about-notifications
Here is another search you can perform to audit any connections created by JAVA specifically using port 1389.
schema:"model_connection" AND direction:outbound AND remote_port:1389
Not a Spyderbat customer yet?
Spyderbat is free to use up to 5 Linux systems. Setup Spyderbat in minutes and start protecting your Linux systems today. Get started!
Write a comment