
While there is a lot of talk about ransomware (for good reasons), many vendors make claims about how they detect ransomware. The thing is, detecting signatures or the behavior of ransomware is already too late to prevent a ransomware event.
Ransomware is very attractive to Bad Actors because it directly monetizes a network intrusion. With data exfiltration, Bad Actors must find methods for monetizing stolen data, such as selling emails or other personal identifiable information (PII) on black markets. Doing so requires using money mules to extract cash from stolen credit card numbers/ATM pins, or committing fraud to extract money directly from stolen PII victims. This all requires work by the Bad Actor. Ransomware provides an immediate opportunity to extract cash directly from the victim of the network intrusion.
Once a ransomware program has access to an internal system, the most common action is to encrypt all or a portion of the victim’s files. The files cannot be decrypted without the key owned by the attacker. For example, according to McAfee the ransomware REvil kills some processes on an infecting machine such as email clients, SQL, and other database servers, deletes Windows shadow copies of files and other backups, then uses an Elliptic-curve Diffie Hellman key exchange to perform file encryption. These actions occur almost simultaneously. There is not sufficient time to prevent the encryption action even when detecting the REvil ransomware program. While other ransomware may use different encryption algorithms (e.g. RSA, AES, ECDH, etc) or encrypt different parts of the system (e.g. Petya encrypts the bootstrap code and master boot record), the overall process is relatively similar with the net result being a quick method for encrypting data and delivering the ransom notice.
Signature-based approaches from Intrusion Detection Systems (IDS) or nextgen firewalls only serve to provide notification that a ransomware event is taking place due to the speed of the encryption process. Bad Actors will also use different/new variants of ransomware to avoid signature-based approaches.
Some security analytics and endpoint detection and response platforms elect to detect behaviors indicative of ransomware rather than signatures. This includes detecting:
- Disabling of shadow copies and stopping critical/backup/SQL services (too late to prevent the ransom event and may generate false positives)
- Specific windows registry calls (too late to prevent the ransom event and may generate false positives)
- Mass encryption of multiple files (clearly too late and possible false positives)
- Traffic to known ransomware command & control (C&C) servers (a cat/mouse game as bad actors update C&C servers).
So while you can detect ransomware from either signature or behavior-based approaches, that often means it is too late to prevent the ransomware event.
That all sounds bad. So what is the good news?
Ransomware still relies on earlier attack stages. Bad Actors have learned that encrypting a random user’s laptop from a phishing attack isn’t very concerning to an organization who can simply restore the system from backup and start over. Instead, Bad Actors perform reconnaissance to learn more about the organization and more importantly what servers/files are considered valuable to target these systems for encryption.
To add more complexity, these three stages: initial access, reconnaissance and discovery, and execution, may be performed by three completely different bad actor groups.
1. Bad Actor Group A performs initial access, sets up persistence and sells the access information to Bad Actor Group B
2. Bad Actor Group B performs reconnaissance, discovers the ‘crown jewels’ and sells the access information and discovery to Bad Actor Group C
3. Bad Actor Group C executes the ransomware event
According to Coveware’s Q2 2020 Report on Ransomware, REvil is now distributed primarily through compromised RDP sessions (65%), phishing (16%), and software vulnerabilities (8%), with many REvil affiliates using brute force attacks. Ransomware-for-service group Darkside, responsible for the recent Colonial Oil and Gas ransomware event, even admits they often do not even know how the initial access took place.
As a result, it is extremely challenging to detect this sequence of activities that span across time and different bad actors.
Tracing multiple stages of an attack has been an Achilles heel for security analytics platforms such as SIEM and XDR. Often alert aggregation uses simple methods (e.g. alerts involving the same host or the same user account within a limited time period). Machine learning for either aberrant or trained attack patterns surface individual activities. Either case generates a high number of false positives, pushing the onus on security analysts to review findings and manually correlate current investigations to any previous alert/investigations. This leads to a game of whack-a-mole with analysts responding to/mitigating individual symptoms of a larger, multi-staged attack without ever fully realizing the complete attack chain to eliminate the threat.
Spyderbat provides a security analyst with all preceding causal activity of an alert from the SIEM or other security tool, including other alerts. The result is a clear view of each stage of the attack and how they are connected, including failed attempts by the bad actor, backdoor installations, etc, regardless of long wait periods in between each action.
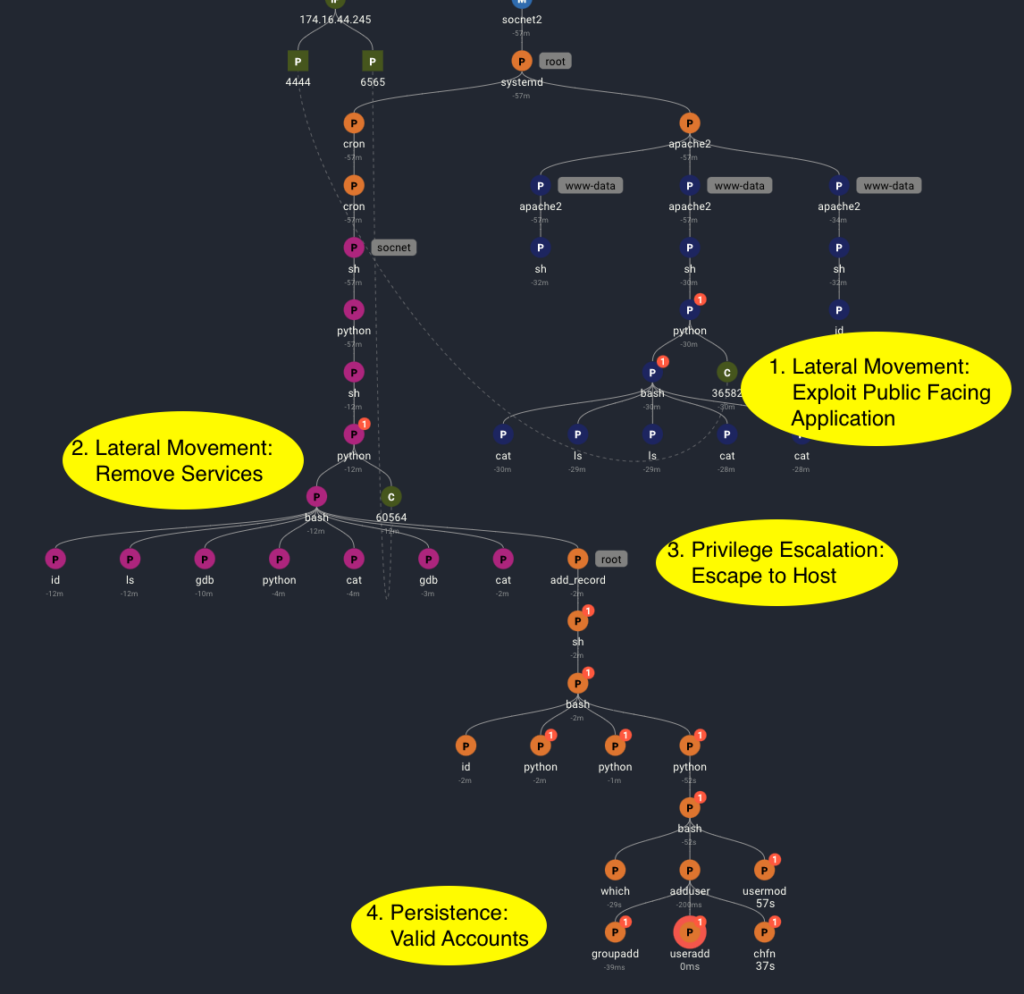
With ransomware, speed is of the essence. Spyderbat’s Attack Tracing and Intercept (ATI) provides security analysts an optimal solution to identify an emerging multi-staged attack with the knowledge to fully remediate the threat before it turns into a ransomware event. Spyderbat eliminates the manual labor and time-intensive exercise of digging through logs, correlating alerts, and reconstructing an attacker’s path through inference and incomplete data. The Spyderbat solution produces an attack trace of all causally connected processes, network activity, user actions, and file access within and across systems. By proactively establishing causal connections, Spyderbat presents to security analysts an immediate, live view of the attack progression, including all causally connected alerts regardless of their priority.
This results in;
- Early recognition of a multi-staged attack where initial activity may not have been detected or previously investigated.
- Immediate interception recognizing the current progression and scope of the attack.
- Full remediation by seeing and removing any previously established persistence left by a bad actor.
- Future prevention from seeing the bad actor’s activity to be able to remove software vulnerabilities or mis-configurations they exploited.
And that’s the most effective approach to head ransomware off at the pass.
Write a comment