Traditional security is constructed in a way that presents analysts with far more information than they could ever be expected to put to practical use, often in the form of log and network data, threat intelligence, and upwards of 10,000 daily alerts. This leads to today’s security analysts working with more data than ever before.
One could go as far as to say that current security workflows have amplified noise at the expense of meaning, and the bulk of this security noise comes from false positives flagged by Security Information and Event Management (SEIM) systems. Approximately 78% of alerts triaged by security teams turn out to be minor undiscovered bugs, poorly phrased code, or simply unidentified network traffic. Nevertheless, a high volume of alerts forces an intractable dilemma on security teams, including:
- Triaging and investigating all alerts, knowing that a high percentage are false positives and that valuable time will be wasted in the process.
- Ignoring alerts, knowing that real, credible threats and attacks are concealed somewhere in the stack.
The risks posed by going down either of these paths will worsen in the near future, especially with the expansion of cloud-based workloads piling onto already disadvantaged security processes.. To extricate cybersecurity from this dilemma, security teams need effective tools to filter the noise so that they can apply their time and skills to real malicious intrusions.
How the Universal Causal Graph Transforms Data in Actionable Insight
Alert-based security platforms require a high degree of sensitivity to deliver measurable results. Sensitivity, however, is a one-way street. Systems can only improve over time by being configured to generate more alerts. Without a parallel development in analytics to weed out false positives, alerts eventually become a kind of unending DDoS attack on the attention of analysts.
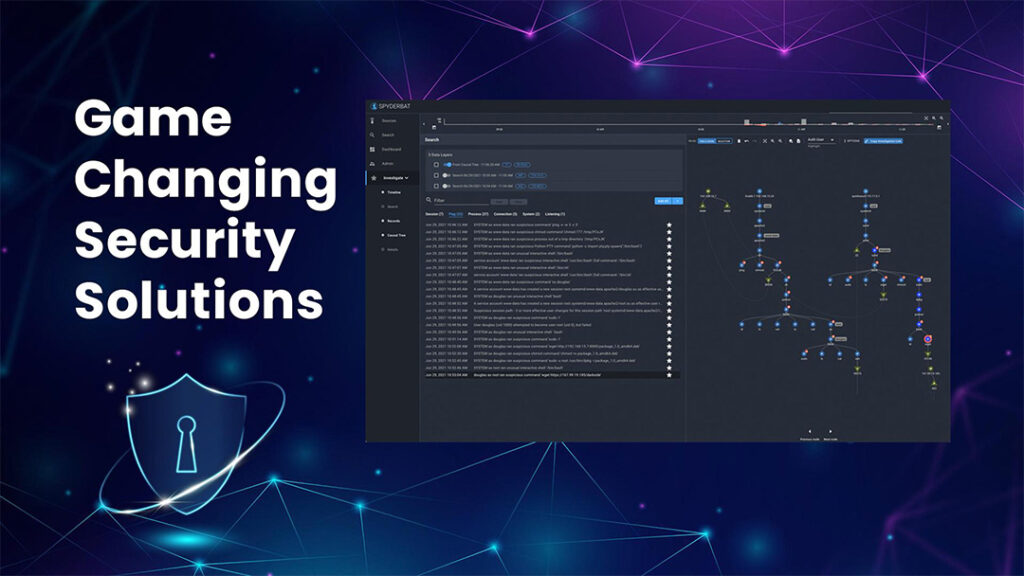
Disrupting this cycle involves seeing alerts and security events in a qualitatively different way. To meet this need, Spyderbat uses a groundbreaking framework to continuously plot all activities (network connections, processes, user activity) with their causal relationships onto a Universal Causal Graph.
The Universal Causal Graph is a live, stream-processed interface where information from all systems is continuously collated into a single, coherent timeline of events – represented as individual nodes – that indicate causal connections up and down the stream. Activities enter the stream with meaningful context, enabling analysts to make connections in a matter of moments where otherwise they would spend days to weeks undergoing investigation.
Spyderbat adds security relevance by ‘flagging’ unusual activities and known threat indicators on the Universal Causal Graph as they occur. While in other security tools these flags would generate individual alerts that would require independent analysis, Spyderbat’s Universal Causal Graph recognizes the relationship of these flags to each other and other activities. These causal connections span across systems, user sessions, and extended periods of time. Spyderbat scores the entire trace, not each flag, to recognize emerging attacks and avoid false positives.
This is how Spyderbat breaks the dilemma of sinking time in false positives or accepting the risks of uninvestigated threats. Routing third-party alerts into the Universal Causal Graph maintains the defensive integrity of SIEM and Intrusion Detection Systems (IDS). At the same time, the live display of causal connections across users, systems, and relative times allows analysts to make rapid, informed assessments of false positives. With the noise filtered, only meaningful contextualized events remain, and real threats can be swiftly and thoroughly eliminated.
Customized Plans for Game-Changing Security Solutions
Spyderbat provides your security teams with unrivaled Linux runtime security and a decisive edge in network security.
To learn more and schedule a demo, contact Spyderbat today.
Write a comment