Last year witnessed an unprecedented increase in software supply chain attacks. According to Aqua Security’s annual supply chain study published in January, this method of cybercrime rose 300% in 2021 over 2020. At the same time, attacks are not just increasing in frequency. They’re also becoming costlier, with the average intrusion into an enterprise’s suppliers and partners now racking up $1.4 million in losses.
Why Supply Chain Attacks Are on the Rise
One growing concern amongst security experts is that supply chain attacks are destined to escalate from current levels. The seeming inevitability of things getting worse before they get better stems from two attention-grabbing observations.
- The weaknesses that supply chain attacks exploit continue to be endemic to systems new and old.
- The stakes are getting higher as even nation-state-level cybercrime organizations have adopted the tactic, in some cases targeting security researchers to steal zero-day exploits from those trying to fix them.
In the first case, experts point to a few common culprits in supply chain exploits.
- Open-Source and Third-Party Vulnerabilities
- Compromised Pipeline Tools
- Uploading of Bad Code to Repositories
While the second two of these three are often the result of misconfigurations or careless practices, open-source vulnerabilities and third-party risks represent a more intractable problem. According to the 2021 OSSRA, the use of open-source code in new applications has increased 259% in the last five years. Meanwhile, reliance on third-party Linux-based suppliers, like Amazon Web Services, has grown by similar leaps and bounds. With these potential vulnerabilities established as mainstays of software development, the security industry can’t expect to train or OpSec their way to a solution. They will have to accept them as permanent features of the threat landscape and engineer better tools to defend networks and platforms that incorporate them.
Spyderbat: A New Solution to Supply Chain Challenges
System-level visibility and early detection are essential to preventing successful supply chain attacks. In today’s increasing patchwork and ephemeral environments of cloud-based third-party servers and services, real-time visibility and monitoring across suppliers have become virtually impossible to sustain with the in-house Linux capabilities most SOC budgets can afford.
Spyderbat takes an industry-first proactive approach to this problem. Rather than retroactively responding to on alerts, where previous actions becoming increasingly difficult to identify, – Spyderbat proactively records all interactions between applications and the processor with their causal relationships, prior to any threat detection. Spyderbat weaves together the totality of these activities in a living Universal Causal Graph (UCG). In the UCG, analysts find an up-to-date, detailed trace capturing every third-party action, software upgrade, and privilege escalation across the whole of your Linux environment.
Operating from this illuminated vantage point, analysts working with Spyderbat immediately recognize emerging attacks, including third-party actions.These capabilities extend to attacks spanning months of activity, even if across ephemeral systems and independently of potentially disabled logging systems.
Take the following example of a threat actor poinsing a software vendor.
- The threat actor poisons a software update.
- You download the software update from the trusted vendor. The download package passes its integrity checks.
- The malware embedded in the poisoned software update waits a randomized time period before activating.
- Once activated, the malware establishes command & control using an algorithm to calculate the domain name and query the IP, communicating over HTTP or HTTPS
- Once C&C is established, the malware attempts reconnaissance and lateral movements.
Your existing security controls, such as SIEM and EDR, may pick up on one of the individual tactics and shut it down – but miss the source allowing the threat actor to try again. Spyderbat sees the totality of actions, all connected based on their causal connections, enabling early identification and complete mitigation.
Here is how the the same scenario looks in Spyderbat:
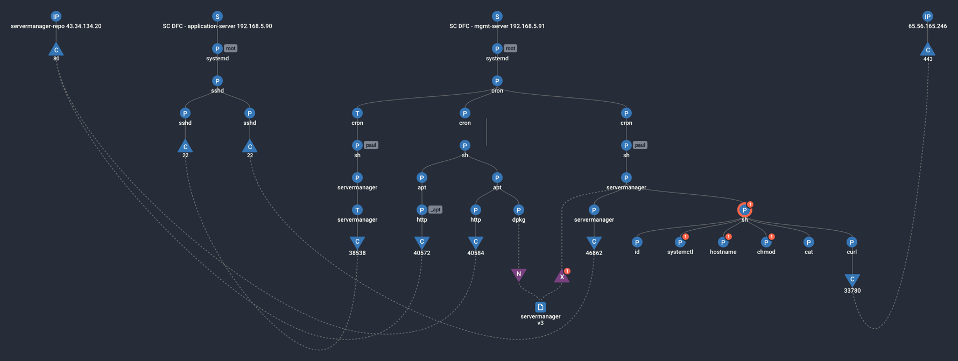
- While suspicous actvities and known MITRE ATT&CK techniques are not recognized until much later, Spyderbat connects the much earlier activity together to accurately identify the point of entry.
- All of the threat actor’s/malware’s activities are aggregated together rather than rely on manual log analysis.
- Spyderbat scores the entire trace by recognizing and connecting multiple techniques with their causal relationships, enabling early recognition of the supply chain attack.
The Spyderbat advantage decimates dwell time and time between detection to root cause identification, allowing analysts to focus on real attacks and instill more exhaustive prevantive measures increasing the security posture of the organization.To experience a personalized demo of Spyderbat’s full capabilities, contact us here.
Write a comment