Cybercrime and security change over time like an evolutionary arms race. Malicious actors probe new vulnerabilities and become increasingly sophisticated in concealing their exploits. Meanwhile, developers patch and refine the ever-expanding volumes of open-source libraries that have become ubiquitous in contemporary software and security experts devise smarter and more discerning intrusion detection systems.
There remains, however, a constant in the back-and-forth technical upmanship in this process – the human actor. At the end of the day, even the most secure and sophisticated systems are governed by human choice. While human behavior is notoriously unpredictable, people exhibit a rather predictable propensity for turning over information – whether maliciously or inadvertently – to the wrong people.
A recent study conducted by Stanford University found that human activity accounts for 88% of data breaches. Of these, 60% involve deliberate criminal actions by individuals within the organization. Security experts call this threat vector the insider threat and it is on the rise with 68% of organizations reporting more frequent insider threat incidents in the last twelve months. As the transition to cloud computing continues, companies are finding it increasingly difficult to detect insider threat activities in their systems.
The Cost and Reach of Insider Threats
A recent study by IBM found that the exposure of a privileged user’s credentials to bad actors results in an average company loss of $750,000. While negligence and failure to follow protocols account for a greater statistical share of insider threat incidents – 62% – those involving complicit insider activity came with a higher price tag of $871,000.
Beyond the potentially catastrophic losses these breaches can incur, organizations and security providers should be aware that the insider threat seems indifferent to scale. Even large organizations that might otherwise be better equipped to rebuff attacks that rely on technical exploits can find themselves blindsided by insider activity.
In March 2022, the cybercriminal organization LAPSUS$ used privileged employee credentials purchased online to gain access to T-Mobile’s servers on several occasions, eventually stealing their source code. Other publicly disclosed targets of similar operations in the last year include Microsoft, Nvidia, Samsung, and Okta.
To put a point on how widespread these tactics have become and the lucrative lure they represent to employees, an expert at Abnormal Security released Telegram conversations he’s had using fake personas representing different organizations. He was directly approached with offers of 40% on $1 million ransomware hauls for installing malware using his credentials.
System-Level Visibility with Spyderbat
Successfully mitigating the insider threat in any organization is a holistic effort involving screening, onboard and continuous training, and rigorous in-house monitoring. Nevertheless, tools like Spyderbat Linux Runtime Security platform give analysts an edge in detecting and deterring malicious insider activity.
Spyderbat maintains a visual record of all system-level activities, even in ephemeral multi-cloud or container-based environments. While ML/AI-based monitoring systems for abnormal user behavior flag anomalous or suspicious user behaviors, well-executed attacks attempt to elude detection by spreading activities out over days to months. The volume of innocous, anomalous user activity often mask real attack activity, while the long time spans between activities foil user behavior analytics in SIEM, or system behavior analytics in EDR.
Individual alerts from SIEM and EDR only capture a single attack tecnhique or anamlous behavior, relying on human manual analysis to capture the dots. Instead, Spyderbat’s analytics track traces of causally-related activity. Analysts working with Spyderbat’s platform for Linux Runtime Security have a decisive advantage, being able to track activities in real-time across user sessions and systems over long periods of time by linking them based on causal relationships.
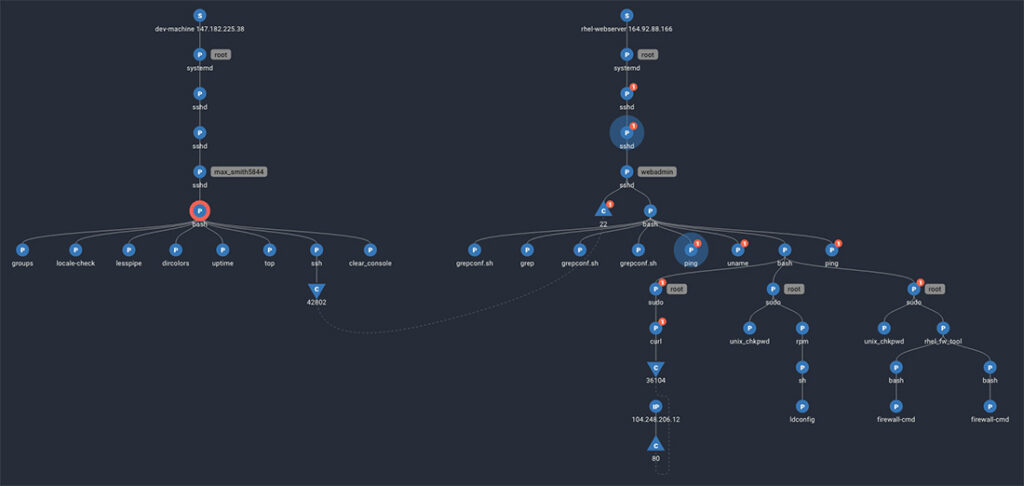
For example, the above Spydertrace captures the user ‘Max’ using a shared account to download and install an unauthorized package.
Instead of investigating hundreds of individual alerts, Spyderbat aggregates causally related security concerns into Spydertraces. Spyderbat automatically re-assesses and re-scores the entire Spydertrace with each new causal activity, even as that activity spans across systems, different user sessions and escalations, and time. By combining even the most benign indicators that may otherwise be missed, the Spydertrace’s causal context and aggregate score accurately recognizes even subtle emerging insider attacks. This is how Spyderbat detects insider attacks otherwise unseen by other security products. And the analyst is visually presented with the entire chain of evidence to immediately understand what is happening and the full scope of the activities.
Spyderbat gives defenders the ability to intervene and shut down attacks in progress while establishing a culture of deterrence that may make potentially bad actors think twice.
To experience unrivaled runtime Linux security, book a demo with Spyderbat today.
Write a comment