The Spyderbat Platform
Gain the superpowers needed to harden your cloud native runtime environments and keep your applications rolling.

What is the Spyderbat Platform?
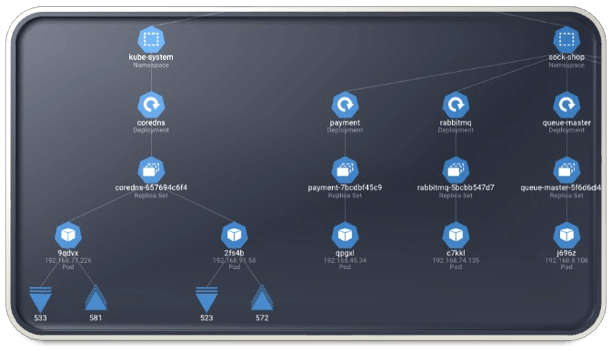
By probing eBPF, Spyderbat builds a map of activities from cloud systems and containers with their causal relationships. Using this CausalContext map, Spyderbat fingerprints workload behaviors, enforces security policies, performs signatureless attack prevention, and provides immediate visibility to root cause.
-

Flashback – Time Travel, the Ultimate Superpower
A continuous runtime digital recorder moving at the speed of light. Whenever you need to go back in time, teleport to the exact microsecond for an OS kernel and container-level trace revealing every step that led to the event. And, you won’t need to wait for an incident to flex your superpower. FlashBack provides early warning signs of troubling traces.
• Eliminate the pain of scanning logs to determine the source of service interruptions and attacks.
• Stop finger pointing by automatically pinpointing root cause.
-

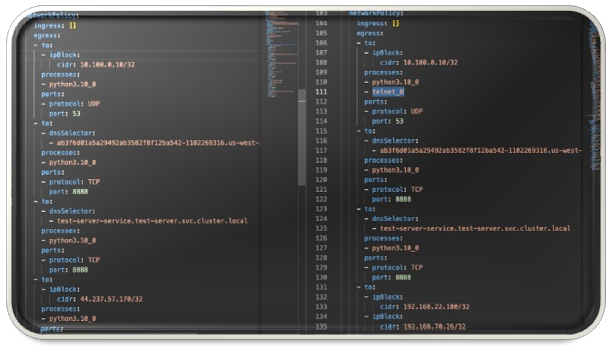
Guardian – Application Drift Has Met Its Match
Spyderbat’s Guardian enables you to accelerate your releases and reduce interruptions. Guardian continuously compares running applications against prior versions, alerts you to application drift, and gives you the insight to take instant action and get your application back on track.
• Enjoy your weekend by avoiding unplanned downtime by patching on your schedule.
• End application drift by automatically comparing runtime execution against prior versions, with the insight to instantly course correct.
-
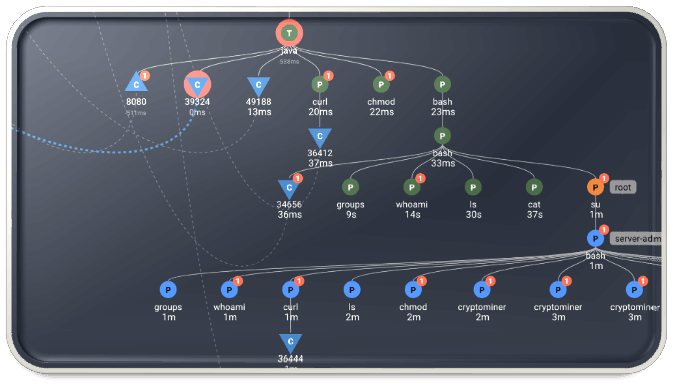
Inteceptor – Detect, Dissect, Destroy
Automated runtime attack eradication stops attackers in their tracks using kernel-level eBPF data to instantly detect and surgically block problematic traces as they begin to unfold. After the action, Interceptor helps you dissect the attack and eliminate the threat from the face of the earth. Batman? Superman? Spider-man? You do you!
• Block attacks targeting known or even unknown vulnerabilities, including,
• Supply-chain attacks
• Data exfiltration
• Malware/Ransomware/Cryptojacking
• Zero-Day attacks
• Stolen credentials/Insider threats
• Eliminate the pain of scanning logs to determine the source of service interruptions and attacks.
-
Value in the first minute
Deploy eBPF Nano Agents in seconds directly or through existing orchestration tools.
-
Visualize and understand
Interactive causalcontext traces expose container and VM workload behaviors to crush investigation time.
-
Ongoing Assurance and protection
Every causal sequence is monitored to automatically detect and stop attacks.
-
Blended workflows
Integrate into existing notification workflows and add third-party alerts to enable SecOps automation (e.g. Slack, PagerDuty).